Category: Security
-
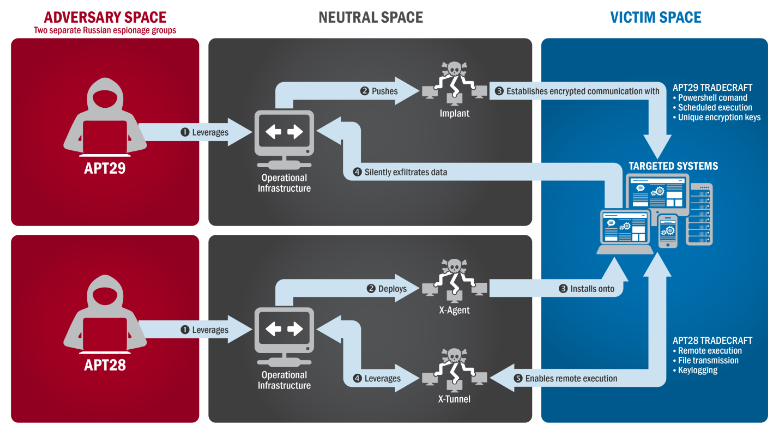
US Government released data that Russia used Ukrainian PHP Malware
The Department of Homeland Security and the Office of the Director of National Intelligence, have released their JAR, also known as a Joint Analysis Report. They called it the GRIZZLY STEPPE JAR. You can read the full publication at https://www.us-cert.gov/security-publications/GRIZZLY-STEPPE-Russian-Malicious-Cyber-Activity or you can download it from our site. JAR_16-20296A_GRIZZLY STEPPE-2016-1229 “The US Government confirms that…
-

DROWN SSLv2 Vulnerability Rears Ugly Head, Puts One-Third of HTTPS Servers At Risk – TrendLabs Security Intelligence Blog
A “new” and important vulnerability has been discovered that affects HTTPS and other services that rely on SSL/TLS implementations. This flaw is in the SSLv2 protocol, and affects all implementations. Researchers refer to this attack as DROWN – short for “Decrypting RSA using Obsolete and Weakened eNcryption”. This attack allows attackers to read or steal information…
-

Ten Laws of Security
Law #1: If a bad guy can persuade you to run his program on your computer, it’s not solely your computer anymore. Law #2: If a bad guy can alter the operating system on your computer, it’s not your computer anymore. Law #3: If a bad guy has unrestricted physical access to your computer, it’s…